As a user, you must protect your computer from harmful viruses, such as Trojans.
Letting a Trojan enter your PC means unauthorized access and data theft. One of the worst kinds of viruses is the Counter.Wmail-Service.Com Trojan.
It is highly malicious software that infiltrates your computer and targets email services.
Its purpose is to compromise the privacy and security of the affected system by routing email traffic through its domain. This can result in the exposure of sensitive data unless stopped.

In this guide, we will tell you the steps to remove this virus from your computer.
Contents
- Understanding The Counter.wmail-service.com Issue
- Signs That Indicate That Your PC Is Infected With The Counter.wmail-service.com Virus
- Steps To Remove The Counter.Wmail-Service.Com Trojan
- Step 1: Use Rkill To Stop Malicious Processes
- Step 2: Remove Malicious Programs From Your PC
- Step 3: Eliminate Malicious Browser Policies From Windows
- Step 4: Clean Windows Of Malicious Files And Folders
- Step 5: Reset Your Browser Settings
- Step 6: Remove Trojans And Browser Hijackers Using Malwarebytes
- Step 7: Use HitmanPro To Scan Your PC
- Step 8: Use AdwCleaner To Delete Malicious Browser Policies And Adware
- Tips To Stay Safe Online
Understanding The Counter.wmail-service.com Issue
It’s crucial to get rid of the Counter.wmail-service.com virus as it is harmful to your computer.
This virus can access sensitive information on your computer and jeopardize your privacy.
If you delay removing the virus, it increases the risks of unauthorized access and data theft, which could seriously harm your system.
When faced with the Counter.wmail-service.com virus, it is important to take prompt action to prevent the trojan from causing more problems.
The Counter.wmail-service.com Trojan, is a harmful virus that sneaks into your system, causing significant damage.
Signs That Indicate That Your PC Is Infected With The Counter.wmail-service.com Virus
Before we proceed with the removal process, it’s important to recognize the signs of this virus.
These signs act as warning signals, helping you to know that your system is infected by the Counter.wmail-service.com virus.
Slow Performance
If you notice that your system is running slowly and becoming unresponsive, it’s likely due to the Trojan running malicious processes and consuming system resources.
Frequent Crashes or Freezes
Trojans have the potential to destabilize your system, causing apps to freeze, and the system to crash frequently.
Changes In Network Activity
Trojans communicate with remote servers to receive commands or send stolen data. Unexpected data usage or unusual network traffic may indicate the presence of the virus.
Trojans can create backdoors for hackers to gain unauthorized access to your system. This poses a risk to your files and data without your knowledge.
Steps To Remove The Counter.Wmail-Service.Com Trojan
Before we start, we’d like to mention that it’s a lengthy process, so make sure to follow all the steps correctly.
We have tried simplifying the steps as much as possible.
Step 1: Use Rkill To Stop Malicious Processes
Start by downloading Rkill and using it to stop any malicious processes that might be active on your PC.
RKill is a tool created by BleepingComputer.com, and designed to terminate malware processes, allowing your regular security program to then scan and remove infections from your device.
When RKill is executed, it terminates malware processes, corrects improper executable associations, and addresses policies that prevent the use of specific tools.
Step #1: To download Rkill, go to the official website, and select the “Download Now” button labeled iExplore.exe.
Step #2: Just so you know iExplore.exe is a renamed version of Rkill.
Step #3: After downloading the program, double-click the iExplore.exe icon to terminate malicious processes. It takes some time for the program to locate and stop various malware processes.
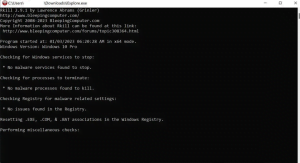
Step #4: Once it’s done, you will see the black window close automatically, and a log file appears on the screen.
Step #5: Instead of restarting your PC, move on to the next step.
Step 2: Remove Malicious Programs From Your PC
This step requires you to find any malicious or unfamiliar programs on your PC, manually.
Sometimes, browser hijackers and adware may have an Uninstall entry that allows for their removal.
Step #1: Open the Settings App by pressing the Windows key + I keys on your keyboard. Alternatively, right-click the Start button and choose “Settings” from the list.
Step #2: In the Settings app, select the option “Apps” followed by “Apps & Features.”
Step #3: In the “Apps & Features” settings, search for malicious or unknown programs.
Step #4: To simplify the process, sort the programs by their installation date. Select the option “Sort by” and choose “Install date.”
Step #5: Identify any suspicious programs, click the three dots beside it, and choose the “Uninstall” option from the menu.
Step #6: Confirm your action by clicking on the “Uninstall” and follow the prompts shown on the screen to complete the process.
Pay close attention to all prompts, as some malicious programs may attempt to include additional items.
After getting rid of the malicious programs from your computer, move on to the next step.
Step 3: Eliminate Malicious Browser Policies From Windows
In this step, we will need the Command Prompt and use it as an Administrator to execute certain commands to get rid of the malicious policies set by malware.
Step #1: Start by typing “cmd” in the search bar. This will launch the Command Prompt as an administrator in Windows.
Step #2: Right-click on the Command Prompt result and choose the option “Run as administrator.”
Step #3: You will see a User Account Control (UAC) prompt appear on the screen, seeking permission to allow the program to run. Select “Yes.”
Step #4: You will encounter a black screen titled “Administrator: Command Prompt.” Now type in the commands and press the Enter key.
Here are the commands you must type:
Type RD /S /Q “%WinDir%\System32\GroupPolicyUsers” and press Enter.
Type RD /S /Q “%WinDir%\System32\GroupPolicy” and press Enter.
Type gpupdate /force and hit the Enter button.
Once you are done with the above steps, move on to the next part of the process.
Step 4: Clean Windows Of Malicious Files And Folders
Now it’s time to manually search and eliminate harmful scheduled folders and tasks on your PC.
You must know that this infection can reinstall itself every 5 minutes after deletion by setting up a harmful scheduled task in the Task Scheduler.
This task could run at regular intervals, stopping you from getting rid of the infection in your system.
Step #1: Find “Task Scheduler” or press Windows + R to launch it. Then type “taskschd.msc” and hit the Enter button.
Step #2: In the Task Scheduler window, go to Task Scheduler Library on the left.
Step #3: Find the suspicious task in the task list, and right-click on it. Then choose “Delete.”
Step #4: In the Windows search, look for “Run” or use Windows + R to access the Run app.
Step #5: Type “%AppData%” in the text box and hit the OK button.
Step #6: In the AppData\Roaming folder, delete any unknown folders. These folders usually appear with names like Travel, Bloom, Default, Energy, and Chrome32.
Step #7: Again, look for “Run” in the Windows search or press Windows + R to launch the Run app.
Step #8: Type in “%localappdata%” and select OK.
Step #9: In the AppData\Local folder, delete the ServiceApp, Default, and WindowsApp folders.
Step #10: Navigate to Google, then to Chrome. From there go to User Data, and then to Default, and then Extensions. Delete any unknown or malicious extension folders.
For your information, this malware can tamper with your browser shortcuts. You must follow these steps to stop it:
Step #11: Right-click on the Start Menu or Google Chrome shortcut on your desktop and choose “Properties.”
Step #12: Under the Shortcut tab, check the “Target” field for any suspicious text related to the AppData folder. Remove such text.
Step #13: The target should only point to the chrome.exe file location. Select the “OK” button to save changes.
Step #14: Use the shortcut to re-launch Chrome, and see if the extension is loading on startup.
Step #15: By manually removing these folders, tasks, and shortcut modifications, you can free your PC and browser.
Step 5: Reset Your Browser Settings
By resetting your browser settings, we will eliminate malicious extensions, and spam notifications, and revert any settings altered by malware to their default state.
It’s important to note that this method will delete all customizations, toolbars, and extensions. However, it will not remove your favorites and bookmarks.
Resetting your Chrome browser settings will reset the new tab page, pinned tabs, startup page, and search engine.
It will also clear temporary data, and disable all extensions while keeping your history, favorites, and passwords intact.
Step #1: Launch Chrome click the three dots located in the upper-right corner, and choose “Settings.”
Step #2: In the Settings menu, choose “Advanced.”
Step #3: Under the “Advanced” section, choose the option “Reset and clean up.”
Step #4: Now select “Reset settings to their original defaults.”
Step #5: Confirm your action by choosing the option “Reset settings.”
Step #6: If a malicious extension persists after the reset, you should reset Chrome Data Sync. Visit chrome.google.com/sync and select the option “Clear Data.”
Step 6: Remove Trojans And Browser Hijackers Using Malwarebytes
By using Malwarebytes you can easily eliminate any adware, infections, or unwanted programs from your system.
Malwarebytes is one of the best anti-malware tools for Windows and is designed to remove or delete various types of malware that software cannot.
The best part is Malwarebytes is free to use, making it a preferred choice for users.
Step #1: Download Malwarebytes from the official website, and double-click on the MBSetup file to install the program on your PC.
Step #2: If prompted by User Account Control, select “Yes” to allow changes.
Malwarebytes might give you two options – a Work Computer or a Personal Computer.
Step #3: After selecting between the two options, hit the “Install” button.
Step #4: After installation, open Malwarebytes and select the “Scan” button.
The program will automatically update the antivirus database and initiate a scan for malicious programs.
Wait for the scan to finish. This may take a few minutes.
Step #5: Once the scan is complete, Malwarebytes will display a screen showing detected adware, malware, or unwanted programs.
Step #6: Click on the “Quarantine” button to remove the identified threats.
Malwarebytes will remove the malicious registry keys and files.
To complete the removal process, Malwarebytes may prompt you to restart your computer.
Step 7: Use HitmanPro To Scan Your PC
Next, we will check your PC using HitmanPro to make sure there are no harmful programs on your device.
HitmanPro is a special scanner that uses a unique cloud-based method for checking for malware.
It looks at how active files behave and examines files in places where malware is often found.
If it identifies a suspicious file that isn’t already known, HitmanPro sends it to its cloud system for examination by two top antivirus engines – Kaspersky and Bitdefender.
Step #7: You can download HitmanPro from the official website.
Step #8: After downloading HitmanPro, double-click on “hitmanpro.exe” or “hitmanpro_x64.exe” to set it up on your PC.
Usually, downloaded files are stored in the Downloads folder.
Step #8: You might see a User Account Control pop-up asking for permission for HitmanPro to make changes to your device. Select “Yes” to proceed.
Step #9: Once HitmanPro starts, you will see the start screen show up. Select “Next” to initiate the scanning process.
Step #10: HitmanPro will now scan your computer for harmful programs.
Step #11: Select the “Next” button.
Step #12: After the scan is complete, HitmanPro will show the malware it found. Click “Next” to make HitmanPro remove the identified items.
HitmanPro might ask you to enable the free 30-day trial to eliminate the malicious files.
Step #13: Click on the option “Activate free license” to start the trial and delete all the harmful files from your PC.
Once everything is done, you will see a screen displaying the status of the programs that were removed.
Step #14: At this point, select “Next”, followed by the “Reboot” button.
Step #15: If HitmanPro doesn’t ask you to reboot, simply select “Close.”
Step 8: Use AdwCleaner To Delete Malicious Browser Policies And Adware
AdwCleaner helps to remove any harmful browser policies and malicious browser extensions.
It is a widely used scanner that excels at detecting and eliminating malware.
It comes equipped with various tools to fix the side effects caused by browser hijackers, adware, and other types of malware.
Step #16: You can get AdwCleaner from the official website.
Step #17: After downloading the setup file, double-click on it to launch the program. The file is named “adwcleaner_x.x.x.exe.”
Step #18: Once the program opens, you will see the license agreement. After reading it, select the option that says, “I agree.”
Step #19: Grant Windows permission to run AdwCleaner, if prompted.
Step #20: Once AdwCleaner starts, go to “Settings” and enable the option “Reset Chrome policies.” This will help remove malicious browser policies.
Step #21: Access the “Dashboard” within the program, and hit the “Scan” button.
AdwCleaner will start the scanning process and detect malware on your system. It may take a few minutes to complete.
Step #22: After the scanning is over, select “Quarantine” to eliminate malware from your PC.
AdwCleaner will now ask you to save the open files before initiating the cleaning process.
Step #23: Select the “Continue” button to complete the removal process.
AdwCleaner will now remove all the malware it finds. After that, it may prompt you to restart your PC.
By the end of this process, your PC should be free of the Counter.wmail-service.com Trojan.
Tips To Stay Safe Online
Here are some easy tips to help you stay safe on the internet and protect your computer:
Keep Your Operating System And Software Updated
Regularly update your apps and operating system whenever there’s a new release.
These updates often include important vulnerability patches, security fixes, and other maintenance.
Use A Good Antivirus
It’s important to have a good antivirus program and make sure it’s always up-to-date.
We recommend using Malwarebytes Premium for extra protection against online threats. Also, make sure that the program is up-to-date.
Be Careful When Installing New Apps And Programs
Before downloading a new app or program, make sure to read license agreements.
Choose advanced or custom options to see if any additional software is being installed.
Be Cautious About What You Download
Cybercriminals may often try to trick you into downloading and installing harmful programs.
You need to be skeptical, especially when downloading new software or apps.
Get An Ad Blocker
Use a content blocker like AdGuard to stop malicious ads, phishing attempts, and Trojans from attacking your device.
An anti-virus program alone is not enough to stop all the threats. You need a good ad blocker too.
Stay Alert
You must stay alert for suspicious messages in messenger apps, email, or phone calls.
Be cautious even if the message appears to be from someone you know.
Use Strong Passwords
Using unique and strong passwords keeps your accounts protected. You should avoid using easily guessable words or personal information in your password.
For additional security, you should enable two-factor authentication whenever possible.
Create A Data Backup
You should regularly back up your files and data so that you don’t lose them if anything happens to your device.
You can create a data backup either manually or automatically using backup software. It’s the best defense against ransomware.
Click Carefully
You should avoid clicking on downloading attachments or links from unknown sources.
These could contain phishing scams or malware.
Avoid Using Pirated Software
Stay away from pirated software and Peer-to-Peer file-sharing programs, as they can compromise your privacy and data.
You must also avoid using cracks, and keygens.
Final Words
Getting rid of the Counter.Wmail-Service.Com Trojan from your system is crucial to keeping your computer safe.
By following the steps mentioned earlier, you can protect your device from potential harm caused by this Trojan.
Taking these steps helps ensure a safer and more secure experience while using your computer.
